IT is set to transform next year. We are already seeing the disruptive beginnings of trends that will continue to expand, forcing organizations and their IT teams to adapt. While there are some perils in not keeping up with the times, as with most technological shifts, firms who stay up-to-date and actively look for advantages stand to benefit. Here is a general digest of the changes coming, as well a list of some individual technologies that bear watching.
1. Ongoing effort versus spurts of work
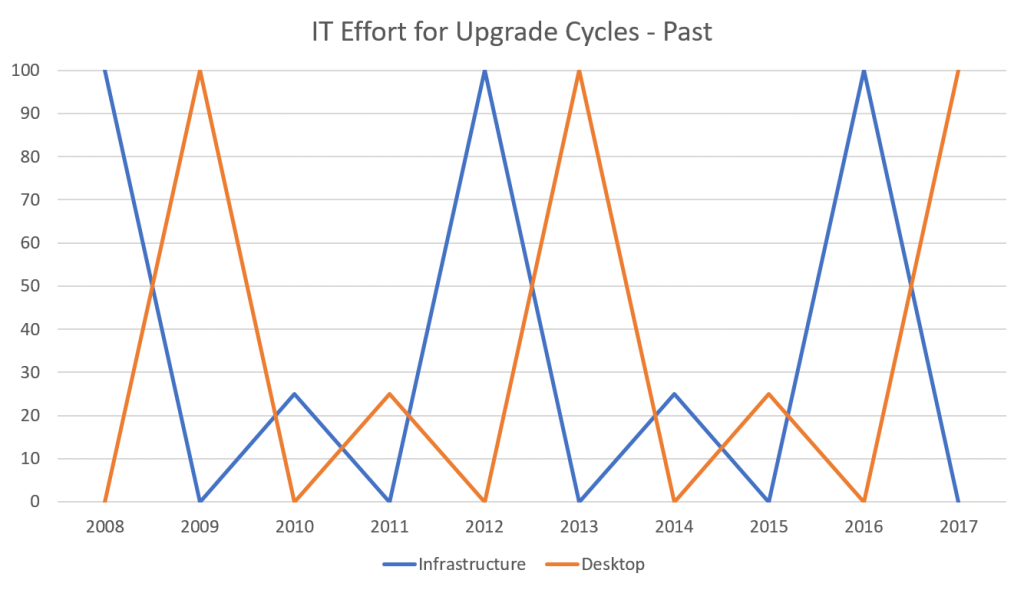
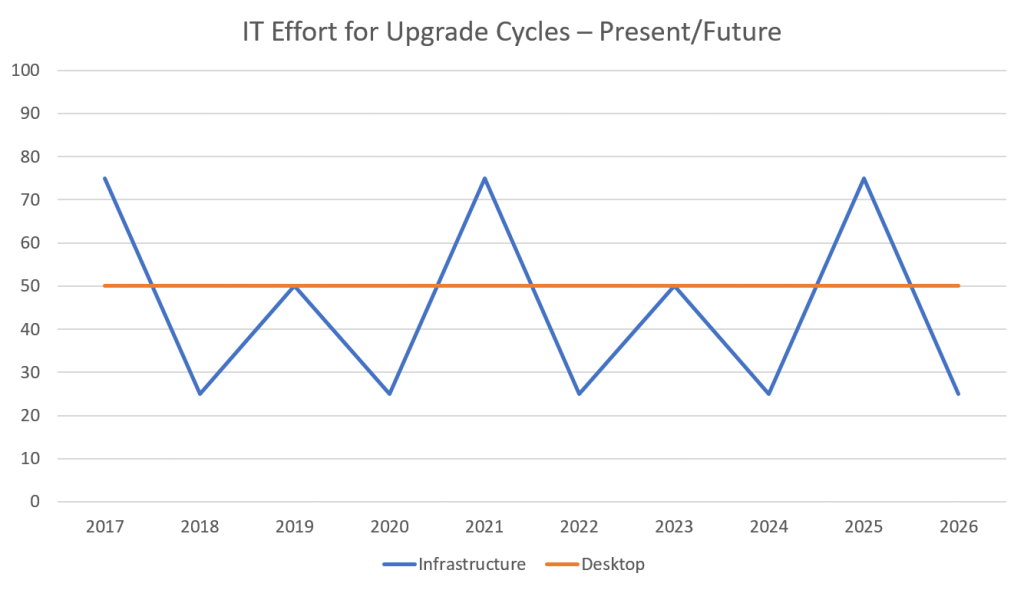
Take a look at the charts below. These are approximate visual representations of the past upgrade cycles IT has had to contend with versus emerging patterns that will dominate upcoming years. It will become increasingly difficult to hold on to the old way of upgrading.
Until the very recent past, IT teams would plan big desktop and infrastructure projects for every four years or so. It was a big effort, requiring all hands on-deck and sometimes consultants to help package, migrate, test, QA, and deploy. Periods in between would be devoted to ongoing IT maintenance and innovation— “putting out fires” and strategic work. For about 15 years, since Windows XP, it was also standard practice to skip around versions of desktop OSs—to go to Windows 7 from XP, for example, or from Windows 7 to 10.
From Windows 10 onwards, things are going to be different. Upgrades will be released twice a year. We recommend that our clients skip one, and no more than two. There will be no avoiding them without putting your firm at risk of security breaches and disruptions of service. IT teams will have the adjust. The good news is that they will no longer experience disruptive spurts of upgrade work that require careful planning and full resource utilization. On the other hand, upgrades will require a constant effort, especially for the desktop OS. Infrastructure work will still wax and wane, but with its own moves to the cloud and consequently to a model of more frequent updates, the line will flatten significantly.
Essentially, the four-year upgrade cycle has become a thing of the past. Yearly cycles are here.
This has several ramifications. Time-consuming and sometimes difficult tasks that had to be scheduled for every few years will now be spread out. Application packaging, to take one aspect of upgrading, used to be a tedious task for every few years that either someone on the staff had to brush up on or a consultant would do. Now it is becoming an ongoing task. Many firms do not have the in-house expertise for it at the moment and will have to adjust their skill sets.
Whereas every big update in the past introduced a trove of new features that required a big training effort, new features will pushed out regularly now. Firms will need a new approach to feature awareness training. In general, these gradual improvements should be easier and less time-consuming for users to assimilate.
Every firm has its own goals and challenges—email us for more information and we’d be happy to discuss your firm’s situation. Kraft Kennedy has developed a new offering called Managed Desktop to help firms with the packaging, licensing, compatibility, and other implications of this new model.
It is not just Microsoft’s products. Enterprise technology is generally moving towards this model, with more vendors offering a SaaS (software-as-a-service) model with off-premise hosting and constant updates (I will talk about this more below). Many firms are moving their document management systems to this model, for instance, and other areas are sure to follow.
2. Security
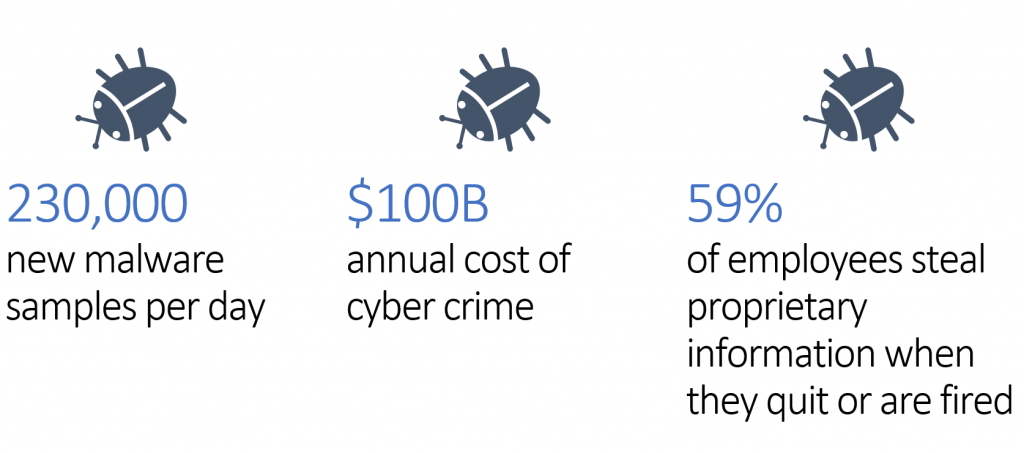
According to Microsoft, 90% of breaches are caused by user error, such as Welcome123 passwords, accidental disclosure of sensitive information, and non-approved SaaS usage (shadow IT).
Three out of ten people will open a phishing email while one of those will proceed to click on the link, possible infecting not only their own computer but the whole firm.
To combat these depressing numbers, modern security programs will center on four fronts:
The Front Door
Securing the perimeter involves protecting your operating system, infrastructure, networks, and email. Patching of these systems is crucial. Every time a patch is released, hackers are gifted a roadmap to attacking your system. Apply fixes as soon as possible to stay ahead of them.
Security awareness training for employees is also necessary. Attackers often try to infiltrate companies by targeting individuals, and phishing campaigns are sometimes not easy to spot, even for the tech-savvy. Security training involves classes for users and periodic testing to determine your organization’s preparedness.
Content
Most companies are in possession of a vast amount of sensitive data. Clients are increasingly asking for the tightest possible security and conducting audits to make sure it’s there.
Documents should be encrypted at rest and in transit—that is, during the time of their creation, sending, and consumption. Vendors are releasing tools to help meet this need, and some are further ahead of others.
Devices
As mentioned above, “Shadow IT,” or unapproved programs on firm-issued or BYOD devices present risks. Firms should employ solutions such as MDM (mobile device management), which controls approved downloads and allows IT to monitor security from a centralized dashboard. As much as possible, these solutions should not impinge on convenience, which leads to the next tenet.
Employee experience
Enterprise security is always a balance of precautionary measures, convenience, and productivity. As security solutions evolve, it is becoming increasingly possible to achieve high levels of security without creating hassles for users. For example, many laptops and phones now come with fingerprint readers, which allow both for a quick sign-in process and a higher level of protection than even a very long password.
3. Cloud Everything
Just a few years ago many companies avoided the cloud, citing concerns about security and availability. Cloud vendors have worked hard to assuage these qualms, and today it is actually difficult to beat the security and high availability offered by many cloud vendors. Exchange Online and Office 365 are prime examples.
More firms will be taking systems to the cloud as the benefits—lower overhead, easier management, constant upgrades—become evident.
To illustrate this, I will describe some aspects of Kraft Kennedy’s setup. We deploy popular and upcoming solutions internally so that we can test them for our clients.
For our DR/BC, we use Veeam backups and Zerto replication. Technologies like Zerto are making it possible for smaller firms to have a level of disaster recovery preparedness that until recently only big firms could afford. Tools like Zerto take Recovery Point Objective (RPO), the main measure of Disaster Recovery, from hours to seconds.
We also entrust our document management, email continuity, and desktop to the cloud with NetDocuments, Office 365 E5, Mimecast, Azure, and AWS.
Organizations such as law firms have very large electronic data repositories. Enterprise search has been a common solution for finding information across these repositories. The next step in this evolution is building processes that can uncover hidden patterns, correlations, trends, preferences, etc.
4. Artificial Intelligence and Machine Learning
AI is being talked about particularly with regard to business development. Various companies are developing tools to help firms find new clients efficiently.
5. Microsoft Teams
Teams is replacing Skype for Business. Although a new Skype for Business server is slated to come out in late 2018, Microsoft will be encouraging Office 365 users to switch to teams. The platform is indicative of what Microsoft is planning for the future. Teams is going to have more of an emphasis on machine learning as well as smoother scheduling options.
6. Information Rights Management integration with DMS
As mentioned above, data should be protected at all stages of its processing, and many vendors are releasing tools to meet these needs. Information Rights Management, or IRM, is technology that offers granular control to access of documents.
7. 5G Wireless Networks
5G looks like it might be a very disruptive technology. It promises to be at least 40 times faster and have at least four times as much coverage as 4G.
8. Apps for Legal
To conclude, I will mention something Kraft Kennedy has developed to help law firms this year.
We noticed many questions to the effect of “Which application are you using for X?” on our Legal IT industry message boards.
To help law firms and legal departments answer that questions, we’ve started Apps for Legal, a free, crowdsourced tool that we hope will help with important application choices. Several dozen firms have created accounts and started to enter data. We encourage you to sign up if you think this might be a useful tool for your firm. Your entries are private and we will absolutely not share your information publicly or with any third-parties.